Summary: Recognizing phishing scams can help small businesses avoid falling victim to these common cybersecurity attacks. In this article, we’ll look at the different types of phishing attacks and what to do if you think your business is being targeted. Cyber attacks against small businesses have become more aggressive since the start of the COVID-19 pandemic, and they’re becoming increasingly difficult to detect. With more and more businesses falling victim to cybersecurity attacks, it is critical to have proper
cyber liability insurance. Additionally, learning
how to prevent a data breach is essential to maintaining a good reputation – and for avoiding thousands of dollars in damages.

The Dangers of Phishing Scams
Phishing is a type of
social engineering scam that attempts to obtain sensitive information using email fraudulently. If you don’t close the loop on your company’s vulnerabilities, you may be baiting the hook the cyber crooks use to catch you unaware and reel in your valuable, sensitive data.
A phishing attack starts with an email that appears to be coming from someone you typically do business with. Although it seems legitimate, you need to be extremely vigilant. If the message format is different in any way or includes red flags like poor grammar, syntax errors, broken links, etc., this could be an indicator of a phishing email. It may be written with a sense of urgency or include a warning that your “account will be closed” or your “access will be limited.” These are both telltale signs of a targeted scam.

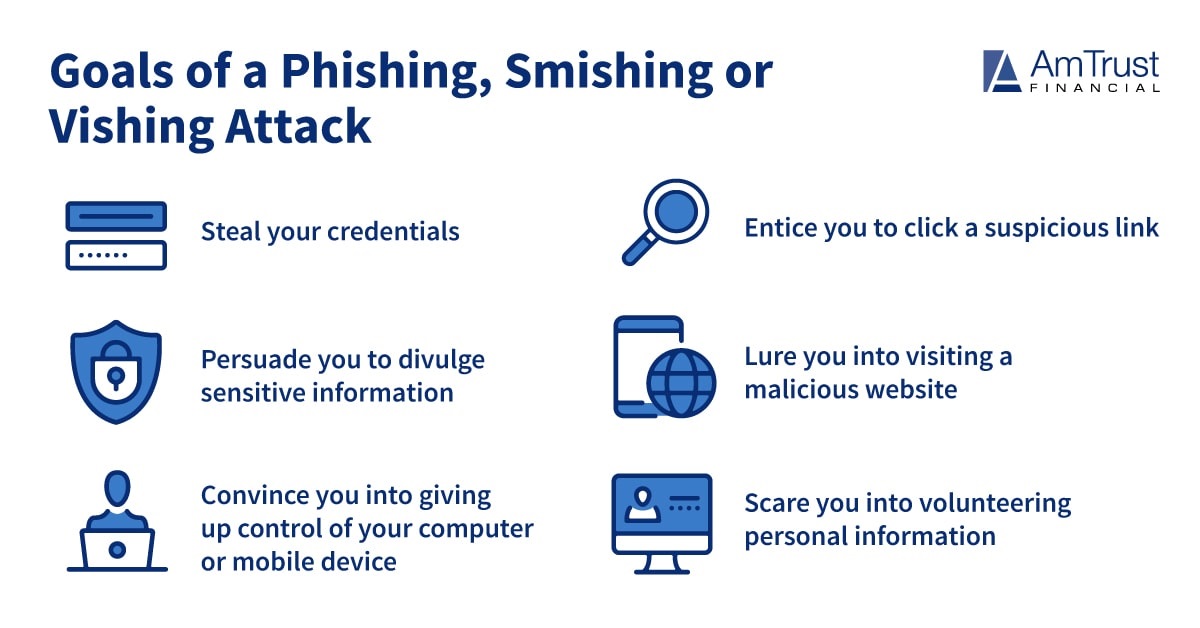
Other Phishing Examples: Smishing and Vishing Attacks
Smishing is a type of phishing attack using texting via short message services (SMS) on cell phones. You might receive a call or text from someone claiming they are support technicians from a well-known company such as Microsoft or Apple, offering to assist with a technical issue you are having. They will attempt to coax you into visiting a website so they “can take care of the problem for you.” The hacker sends a link to download a file containing malware such as a Trojan or
ransomware. They may also ask you to visit a website that is designed to gain access to your computer or device using online collaboration tools similar to WebEx, Microsoft Teams, Slack, Zoom or GoToMeeting.
Vishing is another type of phishing scam carried out by phone and often targets users of Voice over Internet Protocol (VoIP) services like Skype. An email will appear in your inbox that may seem real, with company logos, links and branding, and suggests you click a link to approve something like a financial transaction. The link will then take you to a page that appears to be the company’s website. You’ll be asked to enter your credentials; this information will be harvested and used by the attacker to access your account or your company’s system.
How Cyber Thieves Use Phishing Scams to Steal Sensitive Information
In the old days, phishing emails often came from a faraway place with the promise of millions of dollars for completing some sort of task. These days, identity thieves have gotten smarter. As mentioned above, modern phishing emails or phone calls usually appear to come from a well-known company that many people do business with, such as your bank or a popular software company.
Phishing scams can appear to come from any company, big or small. All an identity thief needs to do is copy an email template and create a look-a-like website – or sound like an IT representative on the phone.
How to Recognize Phishing Scams
What is a common indicator of a phishing attempt? A few of the telltale signs that you may be the target of this type of cybersecurity attacks are:
Private or secure information is requested
Most companies won’t ask you to provide private or secure information from within an email or during a call they made to you. If they do, don’t trust the email or caller. Call your bank and talk to your banker about whether the call or email is legitimate.
The links in a phishing email aren’t valid
Always check links before clicking on them. Slide your mouse over top of the link, and check the address that pops up or appears in the status bar. If the link doesn’t go to the company’s official site, don’t click.
They require the information immediately
Even if you trust the email or phone call, don’t provide any information there when they request it. Instead, open your browser and go directly to the company’s site, rather than clicking the email link. If it’s a phone call, hang up and call the company back using the phone number from their website or your latest statement.

What to do After a Phishing Attack
If you receive what appears to be a phishing email, there are two things you should do: report it and delete it. Alerting your company’s IT security staff of any fraudulent activities can help prevent other employees or business partners from falling victim to the same attack.
The basic steps of reporting a phishing attack are:
- Contact your IT/security department
- Contact the sender of the email or message to confirm if it was legitimately sent
- Verify sender information on the company’s website, especially if it involves financial or confidential data
- Avoid clicking links, attachments or calling the phone number used in the email, as it could be fraudulent
Cyber Insurance from AmTrust Financial
Cyber insurance provides a variety of services to address the modern-day risks and threats of business identity theft and data breach. For more information about cyber liability coverage from AmTrust, please
contact us today.
 This material is for informational purposes only and is not legal or business advice. Neither AmTrust Financial Services, Inc. nor any of its subsidiaries or affiliates represents or warrants that the information contained herein is appropriate or suitable for any specific business or legal purpose. Readers seeking resolution of specific questions should consult their business and/or legal advisors. Coverages may vary by location. Contact your local RSM for more information.
This material is for informational purposes only and is not legal or business advice. Neither AmTrust Financial Services, Inc. nor any of its subsidiaries or affiliates represents or warrants that the information contained herein is appropriate or suitable for any specific business or legal purpose. Readers seeking resolution of specific questions should consult their business and/or legal advisors. Coverages may vary by location. Contact your local RSM for more information.